Top 10 ways to protect your PC and your online account with some of the best and simple steps to keep your computer and online accounts safe from internet crooks
Internet usage is most common in every PC be it your personal computer or at office. Security is the first thing that anyone would be concerned about as internet connectivity has its own pros and cons and hacking is one of the most important concern for most of the PC users. Now, PC users can be relieved of these concerns as below given are some simple steps which they can easily adapt and get their computers and online accounts secured.
- Removal of the pre installed software and apps: With the recent Man-in-the-middle attack in the Lenovo computers the pre installed apps and software really seem to be very dangerous. Most of the times it is just a bloatware, unless user really has some use of all these apps and software hence getting rid of this definitely safeguards the computer against any security threat. Further it is better to get rid of any pseudo antiviruses accompanied with the new computer.
- Choosing a secured web browser : This is an important task as most of the malicious malware comes through the web browser. Setting the right web browser is essential because the correct web browser can help user to safeguard against all the malwares and also help user to use their computer to the best. Depending upon the age of computer and the device that is being used, user needs to choose the correct web browser. Further, Google Chrome is one of the best web browsers which provides additional security via Sandbox feature. If user wants to add further features they can use the Mozilla Firefox extensions also. Basically user needs to know what they want from their browser then check the features and check if the browser meets their requirement then start using that browser.
- Use a strong password for the user account: Setting a strong password is the key for the security of the PC as well as the online accounts. Users must remember certain important points while choosing a password:
- First of all it should be minimum of 8 characters, the longer the better.
- It should be a combination of lower and upper cases of alphabets.
- It should contain random two or three words which should be easy for user to remember.
- Adding numbers, punctuation and symbols will further make the password complicated.
- Never keep the same password for different accounts, instead let the base password remain and user can further add few more words or symbol and hence it will be easy for user to remember the passwords. User can take help of Password Manager in case they feel it is difficult to set different passwords for different account e.g. LastPass free password manager.
- Opting for Virtual Private Networking: Enabling the Hotspot Shield VPN helps user to protect their privacy, secure their internet, get protection against malware, it also enables public Wi-Fi security so any malicious intruders on the same Wi-Fi network cannot access user’s data. This is a free service. Further, OpenDNS services can further add to the browser security from various other malicious sites. The only drawback here is that the internet speed might be slowed down.
- Setting up 2F Authentication for online account: With the cyber crooks at each and every nook and corner, it is always better to set up a Two-Factor authentication for all the online accounts including Apple, Google, Facebook, Yahoo and Microsoft. Here, user needs to use their password for first step of log in and then the account would send a pin number or code to a secured and trusted device like user’s smartphone. This authentication is one of the best security for all the social network sites and a must for all online accounts.
- Protection from the “Phishing Scams”: Online identity theft wherein users give their personal details on illegitimate websites which is then used for various frauds is known as Phishing. There are many ways in which users can safeguard themselves against these Phishing scams. Some of them are listed below:
- Guard against spam: Users need to be cautious of unknown emails sent by unrecognized users, emails that ask personal information, emails that ask any personal or financial information over the internet.
- During online financial transactions always check for “https” rather than “http” as the former is secured site.
- Do not give any financial or personal account details on phone call.Never click on links or download files or open attachments in emails from unknown senders unless you are expecting them from the sender, even if has been sent from some known sender.
- Never send personal or financial information over internet even if you know the recipient of the email.
- Never enter any personal information on any pop-up screen.
- By regularly checking the bank statements and online accounts users can ensure themselves that no unauthorized transactions have been made.
- Be careful of the links that are sent in emails which ask for personal information.
- Most important the computer needs to be protected with proper anti virus and anti spyware software to block the computer against any spyware and malwares.
- Ensuring a strong anti virus software: Users can opt for Anti virus, Anti spyware software and Firewall software for ensuring a stronger security of their computer and online accounts as already seen in the earlier point as this will help user to prevent themselves from Phishing.
- Antivirus software: This basically scans for any strange behaviors and patterns from programs, files and processes and then identifies the threat these malwares can produce to the computer and networks. Basically it needs to be designed in such a way as to detect and deal with the viruses, rootkits, Trojans, keyloggers, worms. Users would need to check if their anti virus software provides real time scanning or is it on demand. Further a regular scanning of the computer as well as regular update of the anti virus software can help user to keep their computer away from all the modern malware. Hence a strong anti virus is a must for all computer users.
- On the other hand Anti Spyware software identifies and removes the unwanted advertising installations from the computer. Firewall Software is a strong barrier in between computer and internet world. This tries to protect the computer from any kind of external malwares and hackers which try to penetrate user’s network with the aim of damaging the computer and also getting personal information of the user.
- Add “HTTPS Everywhere” plugin for all the web browsers: Users can secure their web browser if they use the “HTTPS Everywhere extensions” for web browsers like Mozilla Firefox, Google Chrome etc. This extension has been created by the Electronic Frontier Foundation and the Tor project and hence it is a secured and trusted one. Also it automatically switches majority of the sites from the insecure “http” to “https” and hence protects the user from being hacked or from third party supervision. This extension also provides a secure web page to be viewed and hence increases security of the user. User can thus not only protect their privacy but also can be sure of securing their accounts.
- Anonymous browsing: TOR is a free software and open source system which enables users’ for anonymous browsing. The TOR software shuffles user’s identity due to which any hacker or intelligence agency cannot read user’s browsing history. So with TOR user can ensure their browser security and privacy.
- Ensuring physical security of the PC: Users can opt for the BIOS password and this will ensure that the unauthorized use of the computer is prevented. BIOS is a program that controls the computer’s initial booting cycle as well as the hardware initialization. Remembering the BIOS password by the user is essential because if user forgets the password then it is not possible to boot the computer and it can be reset only with help of the vendor. Users also need to remember to never store any important data on any external USB device or hard drive as these are easily prone to theft. One more method that users can opt for is Encrypting their entire user account and what would this mean, this simply would mean that if user encrypts their data then all the electronic data gets converted into unreadable matter hence it is difficult for the hackers to read the data. Mostly for all the sensitive financial and personal information data encryption is very important. Users can opt for DataMask by AOL which will always protect user’s online identification whenever user communicates online (while shopping or banking or browsing).
These are the few steps that can ensure the protection of computer and online accounts of the user. If readers are already using any other methods for safeguarding their desktops and online accounts from malwares and hackers then please feel free to mention it in the comments section.






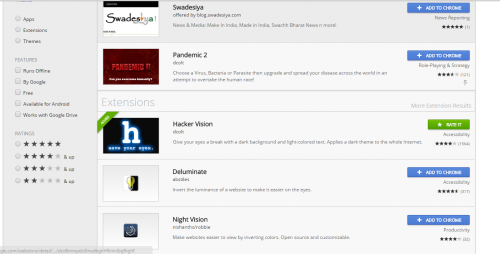 Step 4: Click on the extension if you found it, or
Step 4: Click on the extension if you found it, or 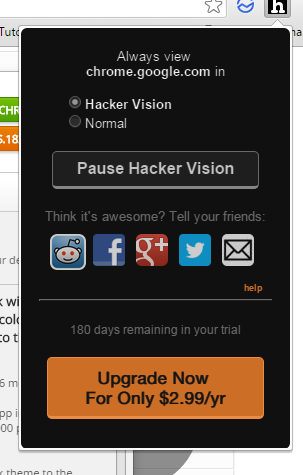 You might be thinking what is the difference between the free and paid version. Actually, there is no difference. You can use the free version for 180 days (6 months), to continue using the app, you need to buy it. Thats all. There is no other difference in both of them.
You might be thinking what is the difference between the free and paid version. Actually, there is no difference. You can use the free version for 180 days (6 months), to continue using the app, you need to buy it. Thats all. There is no other difference in both of them.
